A malicious JavaScript hijack injection has spread across the internet, affecting thousands of websites and forcing them to promote unlicensed Chinese gambling websites. According to experts, roughly 150,000 legitimate websites have been affected so far.
Thousands of Websites Were Hit with a JavaScript Injection
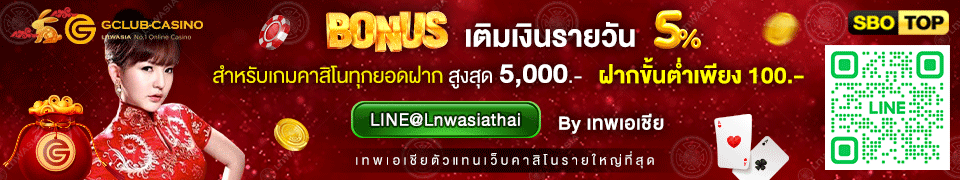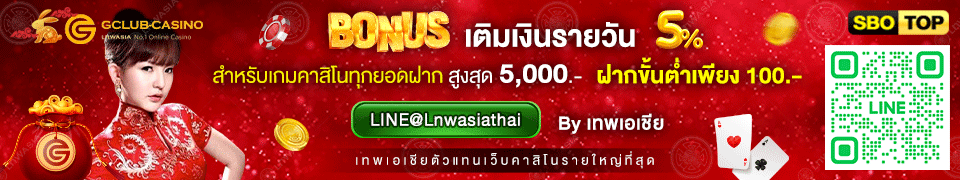
The hackers behind this promotion of illegal Chinese gaming platforms have leveraged iframe injection to display a full-screen overlay on the infected websites, redirecting them to pages promoting gambling. Instead of finding the site they are searching for, customers are thus being greeted by an interface promoting a Chinese gambling website.
Experts said that the overlays sometimes vary from site to site. In some cases, the hackers pose as legitimate betting websites, such as bet365, which recently announced that it will cease its business in China. Similar cases usually employ official gambling company logos and branding to convince users that the offer is legitimate.
C/side expert Himanshu Anand analyzed the threat, saying that despite the slight variations between infected websites, the mechanism is the same. He added that as of the time of his writing, there were over 150,000 infected websites.
Hackers Continue to Adapt
C/side, which is the only autonomous detection tool for assessing 3rd party scripts, specializes in shielding websites from similar fraud. C/side experts first caught wind of the Chinese gambling JavaScript injection fraud in February.
According to Anand, the attack highlights the fearsome adaptability of threat actors, who continue to evolve and scam people. He added that such attacks are on the rise as more and more websites get affected every day.
If you suspect your site might be impacted, review all scripts for hidden HTML entity encoding or suspicious <iframe> injections. As always, ongoing vigilance and regular site auditing remain your best defenses against attacks like these.
Himanshu Anand
In c/side’s official release, Anand provided further insights into the mechanisms of the scam.
Cybercrime Remains a Significant Threat
Speaking of cybercrime, a recent cyberattack on Merkur, one of Germany’s most iconic gaming operators, triggered concerns regarding data protection. As it turned out, several websites were affected, including Slotmagie, Crazybuzzer, and Merkurbets.
Merkur believes that the bad actors were not interested in misusing consumer data but asked its clients to remain cautious and vigilant.
Elsewhere, Interpol cracked on a cross-border criminal syndicate spanning several African countries. The initiative, known as Operation Red Card, led to the arrests of some 306 people, some of which might have been victims of human trafficking.